The Best Honeypot Software
Chasing bad guys can be an exciting and fun activity that can be achieved in many different ways. One of the best ways to chase bad guys is through the use of the best honeypot software.
If you are a target for financially motivated cyber criminals or nation-state-grade attackers, you might need deception technology to save your ass. The best honeypot software have been around for many years and have recently become the secret weapon of threat hunters and purple teams worldwide.
In this post, we will explain what a honeypot is, how it works, how to use it and the list of the best honeypot software, both free and paid. Before I list the best honeypot software, let’s get familiar with honeypot software.
Now, I know you want to know what is honeypotting. Here is what you want to know.
READ ALSO: 18 Best PC Cleaner Free – Speed Up Your PC With A Few Clicks
What Is A Honeypot / What Is Honeypotting? (Free Honeypot Software)
what is honeypotting? Honeypot software is a PC application or system created to attract malicious agents trying to attack PC networks through the use of phishing, DDoS, spam and other nefarious methods.
Once an attacker falls into this trap, the honeypot lets the administrators obtain valuable data about the type of attacker, what the attacker was trying to do and identify the attacker.
The main reason you need a honeypot is to identify emerging attacks against your system’s software and collect reports to analyze and generate intelligence data that you can use to create prevention methods against threats.
We have two types of honeypots which include:
- ProductionHoneypot: This type of honeypot is used by public and private institutions, corporations and companies to investigate the behavior and methods of hackers seeking to attack networks on the Internet
- Research honeypot: This type of honeypot software is used by developers, blue team managers and system administrators working in institutions like schools, universities, colleges and other related associations.
Essentially, the best honeypot software lets you collect important data needed to work on different attack surface reduction techniques.
What Are The Advantages And Disadvantages Of Honeypots and Honeynets
Benefits Of Free Honeypot Software (Honeypot Companies)
- Honeypot software remains an excellent way to learn the techniques attackers employ to target your network
- It is cost-effective because you can use an old computer to make it and there is high-quality, Free Honeypot Software you can use
- Because the only communication with honeypots is hostile, it is easy to review the logs
Disadvantages Of Honeypots (Free Honeypot Software)
- Finger Printing: Because of the behavior or characteristics of honeypots, attackers often recognize them
- Limited field of views: Honeypots can only see activities directed against them
- Honeypots introduce risk into the environment: When bad guys attack and compromise a honeypot, they can use it to attack other organizations or systems if not figured out properly.
READ ALSO: The Best Free Backup Software Reddit
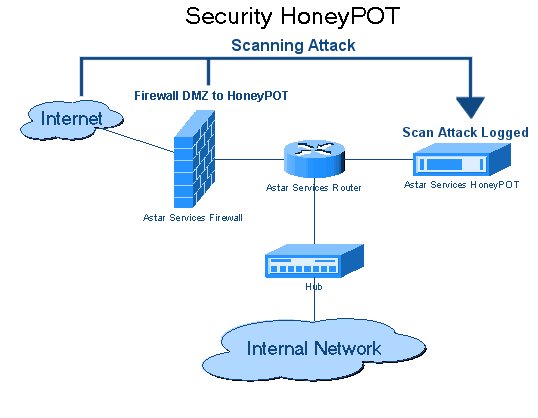
How Does The Best Honeypot Software Work? (How Honeypot Works?)
Honeypot is a trap system and it is often set up in a cloud server or VM connected to a network, but isolated and strictly monitored by network teams and system. To help them get noticed by the hackers, honeypots are created to be intentionally vulnerable, with weaknesses an attacker will detect and try to exploit.
Such weakness could be part of a security vacuum inside an application or system vulnerability like unnecessary open ports, a weak password, outdated software version or an old unpatched kernel. once the attacker finds a vulnerability, he will try to launch an attack until he gains certain control of the application or box.
While the attacker is trying to exploit the vacuum, the honeypot administrator is watching every step carefully, collecting data from the attacker that will help to harden current security policies. In this case, the administrator can report the attacker’s activities to legal authorities, which is what high-end corporate networks usually do.
Some honeypot software work as a trap that distracts attackers from vital data that’s hosted on the actual network. When you are configuring your honeypot software, you need to be aware of the level of hacking difficulty you plan to expose to the attacker. If it is not hard for them to hack, they may lose interest.
Also, if you harden the system for the attacker too much, you will thwart any attacks and will not be able to collect any data. You should also know that some savvy attackers may detect when they are inside a honeypot.
In fact, non-technical users can detect honeypots using automated honeypot detectors like Honeyscore, which identifies honeypot IP addresses.
READ ALSO: 13 Best Torrenting Software Reddit To Try
Examples Of Honeypot (Best Honeypot Software)
Some system engineers classify honeypot based on the targeted software they are trying to expose or protect. So while the list could be long, but here are the most popular:
- Malwarehoneypot: This is designed to simulate vulnerable apps, systems and APIs for the purpose of getting malware attacks.
- Spider honeypot: This honeypot is created to help block malicious ad-network crawlers and bots.
- Database honeypot: Designed to find web attackers.
- Spam honeypot: Works with RBL lists to block malicious traffic

The Best Honeypot Software (Honeypot Companies)
There are many honeypot software out there but we have collated the best honeypot software here for you. These applications are a must for blue and purple teams. Some of the software are open-source software.
1. SSH Honeypots
- Cowrite: Cowrite is a medium interaction SSH honeypot that works by emulating a shell. The software provides a fake file system that is based on Debian 5.0, allowing you to add and remove files as you wish. It also saves all the uploaded and downloaded files in a quarantined and secure area, so that you can easily perform analysis if needed. The software can also be used as SSH and Telenet proxy and lets you forward SMTP connections to another SMTP honeypot.
- Kippo: Kippo is another SSH honeypot software written in python to detect and log brute force attacks, as well as the complete shell history performed by the attacker. This software provides a fake file system and the ability to offer fake content to attackers (e.g. user password files) and a powerful stat system known as Kippo Graph.
2. HTTP Honeypot
- Google Hack Honeypot: Known as GHH, this software emulates a vulnerable web app that can be indexed by web crawlers but remains hidden from direct browser requests. The transparent link used prevents the honeypot from being found by the attacker. This allows you to test your app against Google dorks. This software provides an easy configuration file and logging capabilities for getting critical attacker information such as user agent, IP and other details.
- Nodepot: Nodepot focuses on Node.js and allows you to even run it in limited hardware like Raspberry Pi/ Cubietruck. If you run a Node.js app and want to get important information about any incoming attack and discover how vulnerable you are, this is the best honeypot software for you.
- Glastopf: Glastopf is an HTTP-based that allows you to detect several types of vulnerabilities, including remote and local file insertion and SQL injection (SQLi) as well as using a centralized logging system with HPFeeds.
3. WordPress Honeypot
- Wordpot: Wordpot is one of the most effective WordPress honeypot software that can be used to boost WordPress security. The software helps to detect malicious signs for themes, plugins and other common files used to fingerprint a WordPress installation. It is written in Python, easy to install and can be handled from the command line without any hassle. The software lets you install custom Wordpot plugins.
- Blackhole For Bad Bots: This software is designed to avoid automated bots from using unnecessary bandwidth. It means it lets you detect and block bad bots. It works by adding a hidden link in all your pages’ footer to catch bad bots. Once a bad bot is caught, it’ll be blocked from accessing your site.
- Formidable Honeypots: This honeypot is one of the most famous honeypots used with WordPress. It is not visible to humans but will effectively detect bad bots. This does not require any configuration as you only need to activate the plugin and it will automatically be added to all the forms you use in WordPress, whether pro or free versions.
4. Database Honeypots
- MongoDB-HoneProxy: This is a honeypot proxy that can run and log all malicious traffic into a third-party MongoDB server. To get this software working perfectly, you need GCC, Node.js, g++ and a MongoDB server. It can be run inside a Docker container or other VM environments.
- HoneyMysql: Created to protect SQL-based databases, this software is a simple MySQL program that is written in Python. It can be installed easily and it works on most platforms.
- ElasticHoney: This is an effective honeypot that allows you to catch malicious requests attempting to exploit your RCE vulnerabilities. The best thing about this honeypot software is that it is available for both Linux and Windows operating systems.
5. Email Honeypots
- SpamHAT: Designed to catch and prevent spam from attacking your inbox, this is a great software for you. Be sure to have Perl 5.10 or higher installed to get this honeypot to work properly. You may also need to install some CPAN modules like Mail::MboxParser, Digest::MD5::File, IO::Socket, LWP::Simple, DBD::MySQL, LWP::UserAgent, as well as having a running MySQL server with ‘spampot.’
- Mailoney: Mailoney is an excellent email honeypot written in Python. You can run it in different modes including pstfix_creds, open_relay and schizo_open_relay.
- Honeymail: This is the best honeypot software for stopping SMTP-based attacks. Written in Golang, this software will allow you to set up numerous features to detect and prevent attacks against your SMTP servers. It also offers you powerful DDoS protection against massive connections. A few of its features include, the ability to configure custom response messages, storing emails in a BoltDB file, enabling StartSSL/TLS encryption and extracting attacker’s information like source domain, attachment, country and email parts (TXT or HTML).
6. IOT Honeypots
- Kako: This software works to capture attacking information from all incoming requests, including the full body. It includes HTTPS, HTTP, Telnet servers. The software requires python’s Boto3, Cerberus, Click and Requests to work.
- HoneyThing: Designed for the Internet of TR-069 enabled service, HoneyThing is software that works by acting as a full modem/router running the RomPager web server and supports TR-069 (CWMP) protocol. HoneyThing can emulate popular vulnerabilities for Misfortune Cookies, Rom-0, RomPager and more. This software also provides an easy and polished web-based interface. It provides support for TR-069 protocol.
7. All-In-One Honeypots
- Honeydrive: Honeydrive is a GNU/Linux distribution that comes pre-installed with a lot of active defense capabilities.
- MHN: This combines Kippo, Conpot, Dionaea and Snort and wraps them for easy installation and use.
Other Useful Honeypot software (Honeypot Companies)
Note: If you are setting up a honeypot in your live infrastructure, you are going to be exposed to a very high level of incoming attacks and be playing with fire. Smart attackers can spoof and hide behind the legal network traffic to hack you. Be careful!
READ ALSO: Guide to Apple Device Security: These Tips Will Keep Threat Actors at Bay
Honeypot Detection Tools
Honeypot detection tools are used to detect honeypots and take action. They are mostly used in the cybersecurity field.
Honeypot detection tools can be classified into three types:
- Signature-based: a signature is created for each honeypot that is detected and then it is compared with any new honeypots. This type of tool is not very accurate because it doesn’t differentiate between legitimate and malicious traffic.
- Behavioral analysis: this type of tool uses machine learning to analyze the traffic generated by a honeypot and then classify them into legitimate or malicious based on behavior.
- Signature-less: this type of tool uses machine learning to analyze the traffic generated by a honeypot without creating any signatures for them beforehand. The accuracy of this type of tool depends on how well the machine learning model is trained.
Honeypot detection tools are used to detect when honeypots are being monitored. These tools are essentially a type of malware that can be installed on the victim’s computer and monitored for any changes in the victim’s system.
Honeypot detection tools have been around for a long time, but they haven’t been able to keep up with the rate of change in hacking techniques. Here are a few honeypot detection tools:
1. Hping
Hping offers a command-line-oriented TCP/IP packet assembler/analyzer. It can send ICMP echo requests and its interface is inspired by the ping (8) UNIX command. It supports ICMP, UDP, TCP and RAW-IP protocols. It features a traceroute mode, the ability to send files between covered channels and more.
Though Hping has been only used as a security tool before, you can use it in many ways to test networks and hosts. Other things you can do with Hping are:
- TCP/IP stacks auditing
- Remote uptime guessing
- Remote OS fingerprinting
- Advanced traceroute, under the supported protocols
- Manual path MTU discovery
- Network testing, using varied protocols, TOS, fragmentation
- Advanced port scanning
- Firewall testing
- It is also useful for students learning TCP/IP
Hping works perfectly on Unix-like systems including Windows, macOS X, Solaris, OpenBSD, FreeBSD, Linux and NetBSD.
2. Nessus
Nessus is the global standard when it comes to vulnerability assessment. This honeypot detection tool helps you to know your vulnerability and disrupt attack paths.
Nessus is a vulnerability scanner that checks for security vulnerabilities in your network. It is one of the most popular tools used by system administrators to keep their systems secure.
Nessus Honeypot detection tools are a set of scripts that can be run to detect the presence of honeypots on your network. The scripts are designed to detect whether or not the host has been compromised, and if it has, what type of compromise it is.
Honeypots are a form of computer security defense that involves setting up an intentionally vulnerable computer for surveillance purposes. They can be used to lure attackers into revealing themselves so they can be detected and stopped from entering your network.
The main purpose of this software is to provide an additional level of protection against hackers who might try to use these vulnerabilities in their attacks.
Nessus is efficient and can be deployed on any platform, regardless of where you are or who you are. It is perfect for educationists, organizations and individuals.
3. Apponic Send-Safe Honeypot Hunter
Send-Safe Honeypot Hunter is created for checking lists of SOCKS and HTTPS proxies for honeypots. Here are the features of Send-Safe Honeypot Hunter:
- Helps check different remote or local proxy lists at once
- Checks the list of SOCKS4, SOCKS5 and HTTPS proxies with any ports
- Processes proxy lists automatically every specified time
- Can upload valid proxies and “All except honeypots” files to FTP
- Works for usual proxy list validating
How To Install And Configure A Honeypot Software On Your Network
How To Monitor And Analyze The Data Collected By A Honeypot Software
Monitoring and analyzing the data collected by a honeypot software is a crucial aspect of honeypot deployment. It allows you to gain insights into potential threats, attacker behavior, and emerging trends. Here’s a guide on how to monitor and analyze honeypot data:
1. Data Sources
Honeypot data typically comes from various sources:
- Logs: Honeypot software generates logs that record all interactions and activities. These logs can be rich sources of information.
- Alerts: Honeypots can trigger alerts when specific conditions are met. Alerts can indicate potentially malicious activity.
- Network Traffic Capture: In some cases, you may capture network traffic, including payloads, for in-depth analysis.
2. Tools and Techniques
- Log Analysis Tools: Use log analysis tools such as ELK Stack (Elasticsearch, Logstash, Kibana) or Splunk to parse, index, and visualize the log data.
- SIEM (Security Information and Event Management) Systems: These systems provide centralized monitoring and analysis of security events.
- Intrusion Detection Systems (IDS): IDS systems can be used in conjunction with honeypots to correlate and analyze data.
- Packet Capture and Analysis Tools: Tools like Wireshark can be used to analyze network traffic captures.
- Custom Scripts and Programs: You can write custom scripts to parse and analyze honeypot logs for specific patterns or activities.
3. Interpreting the Data
To effectively interpret the data collected by a honeypot, follow these steps:
- Identify Patterns: Look for patterns in the data. This may include repeated access attempts to certain ports, IP addresses, or specific attack techniques.
- Detect Trends: Over time, observe trends in attacker behavior. For example, you may notice an increase in attacks during certain hours or days.
- Analyze Attack Sources: Determine the geographic origins of the attackers and identify common IP addresses, domains, or networks associated with malicious activity.
- Methods and Motives: Analyze the methods used by attackers (e.g., scanning, brute-force attacks) and attempt to deduce their motives, whether it’s reconnaissance, data theft, or disruption.
- Payload Analysis: If network traffic is captured, examine payloads to understand the nature of attacks. This could include malware samples or exploit attempts.
4. Real or Simulated Attack Examples
Here are a few examples of what you might discover through honeypot data analysis:
- Port Scanning: You might observe repeated scans of your network for open ports, which can indicate an attacker trying to identify potential vulnerabilities.
- Brute-Force Attacks: Honeypot logs may show numerous login attempts with various usernames and passwords, indicating a brute-force attack.
- Malware Distribution: By analyzing payloads, you might identify an attempt to distribute malware through the honeypot.
- Zero-Day Exploits: The honeypot could reveal novel or zero-day exploit attempts, which can be of high significance for threat intelligence.
- Command and Control (C2) Activity: If the honeypot emulates a system that could be compromised, you might detect C2 communications.
5. Reporting and Visualization
Create reports and visualizations to share findings and insights with your team or organization. Use charts, graphs, and tables to make the data more understandable. Reports can be valuable for security management and decision-making.
How To Use A Honeypot Software To Improve Your Network Security
Using honeypot software can significantly improve your network security by providing valuable insights into attackers, their techniques, targets, and vulnerabilities. Here’s how to effectively use honeypot software to enhance your network defenses:
1. Gather Valuable Information
Honeypots can provide the following information:
- Attacker Profiles: Learn about the origin, frequency, and characteristics of attackers targeting your network.
- Attack Techniques: Understand the methods and tools attackers employ, including scanning, probing, and exploiting vulnerabilities.
- Targeted Systems and Services: Identify the specific systems, ports, and services that attackers are interested in.
- Vulnerabilities: Discover which vulnerabilities are being targeted, potentially highlighting weaknesses in your network.
2. Improve Network Security
Once you’ve collected data from your honeypots, use this information to enhance your network security:
- Update Firewall Rules: Adjust your firewall rules to block IP addresses that repeatedly attempt unauthorized access.
- Patch Systems: Prioritize and apply security patches to the systems and services that attackers have targeted, reducing potential vulnerabilities.
- Strengthen Passwords: Review the honeypot data to identify common password attack patterns. Encourage the use of strong, unique passwords.
- Enhance Intrusion Detection Systems (IDS): Configure your IDS to recognize attack patterns observed in honeypot data and trigger alerts.
- Harden Systems: Apply hardening measures to reduce the attack surface, such as disabling unnecessary services and securing configurations.
- Implement Multi-Factor Authentication (MFA): Wherever possible, implement MFA to add an extra layer of security to your systems and accounts.
- Encrypt Sensitive Data: Use encryption for sensitive data to protect it from exposure in case of a breach.
- Train and Educate Staff: Educate your staff about the threats and attack techniques observed in honeypot data. Promote a security-aware culture.
3. Best Practices for Using Honeypots
To use honeypot software effectively and safely:
- Isolate Honeypots: Isolate honeypots from your production network to prevent accidental exposure of real systems.
- Monitor and Analyze Regularly: Continuously monitor and analyze the data collected by your honeypots. Schedule regular reviews to identify trends and threats.
- Keep Honeypots Updated: Maintain and update your honeypots to ensure they emulate the latest systems and services accurately.
- Use Multiple Types: Deploy different types of honeypots (e.g., low-interaction and high-interaction) to cover a wide range of threat scenarios.
- Legal and Ethical Compliance: Ensure your use of honeypots complies with legal and ethical standards. Consult your organization’s legal team if needed.
- Segmentation: If applicable, segment your network to separate sensitive systems from honeypots and potentially malicious traffic.
- Information Sharing: Collaborate with threat intelligence sharing communities to contribute data and gain insights from others.
- Documentation: Maintain clear documentation about your honeypot deployments, configurations, and findings.
- Incident Response Plan: Develop an incident response plan to handle and mitigate real security incidents effectively.
- Regular Review: Periodically assess the effectiveness of your honeypot deployments and adjust your security strategy accordingly.
Honeypots are valuable tools for improving network security, but they should be used as part of a broader security strategy. When implemented and maintained correctly, honeypots can help you stay one step ahead of attackers and protect your network from emerging threats.
Free Honeypot Software For Windows
Honeypot software is a type of anti-malware software that is designed to attract and trap malware by setting up fake files and folders.
Honeypots are a part of the security research community that focuses on computer network defense. They are used for both defensive and offensive purposes, such as detection, identification, tracking, and even exploitation of malicious activity.
The honeypot software for Windows is an application that will help you protect your system from malware attacks.
Here is free honeypot software for Windows:
Honeypot GitHub
Honeypot GitHub is a project that was created by the developers of the Honeynet Project. It is designed to lure hackers who are looking for vulnerable sites. The project’s main goal is to collect data on how hackers are searching for targets and what methods they use.
The idea behind this project was to create a fake site that would look like a real one, but it would be vulnerable and have some fake content in it. The goal of the site is to lure hackers, so they can be tracked down and caught.
You can check out all the best honeypot GitHub here.
Honeypot Project Ideas
Honeypots are a type of security measure that can be used to detect and track intruders. They are often deployed on networks to monitor traffic and identify malicious behavior.
I will be discussing some honeypot project ideas that can be implemented in a corporate environment to detect cybersecurity threats.
- Create a fake website for your company and see if it gets any hits from potential hackers.
- Monitor your employees’ computer activities by tracking their keystrokes, mouse movements, or any other activity on their computers.
- Place fake files on your network drive so you can see if anyone tries to access them or download them without permission.
Here is how o build a honeypot:
- Install the honeypot software. Do not use admin accounts with access to vital systems. so use a different account. Do not store vital data on the server, instead use decoy data. Also, isolate the physical server from the rest of the network.
- Configure firewall and logging policies
- Configure the honeypot
- Test it
Linux Honeypot
network. They are usually deployed in networks to detect malicious attack patterns and network intrusion.
The Linux honeypot is an open-source project that was created by the Honeynet Project. It is a Linux distribution that can be used to create a virtual machine or server, which can then be used as a honeypot.
High Interaction Honeypot
A high interaction honeypot is configured to act as a production system and created to provide attackers with full reign of an operating system as the attackers are lured to compromise the system.
This system is configured to use extensive system and file system logging which is subject to an exhaustive set of IDS rules and monitoring.
Honeypot Vs Honeynet
Honeypot is a security setup usually created as a virtual trap to lure attackers and learn how they attack and what they are looking for. It is an intentionally compromised computer system that lets attackers or hackers exploit vulnerabilities so that the organization can study and improve security policies.
On the other hand, a honeynet is a decoy containing one or more honeypots that look like a real network. It contains multiple systems hosted on one or just a few servers, where each represents one environment.
So, any system created on honeynet may work as a point of entry for hackers. A honeynet is created to gather intelligence on hackers and divert them away from the real network. However, honeynet has an advantage over simple honeypot because it feels more real and has a large area to catch attackers.
Is Honeypot Good For You?
Now, you may be thinking, “is honeypot good for you?” While no system is perfect, you should still try honeypot if you want to improve the security of your company. In simple terms, the honeypot is good for any organization that wants to improve security.
As stated above, honeypot offers a lot of benefits such as:
- Ability to observe how hackers work
- Create profiles for hackers who are trying to hack into your organization’s security system
- Gather intelligence on attack vectors, exploits and malware and train your IT staff with it
- Waste hacker’s resources and time
- Improve security system
However, you should be cautious when using honeypots. Make sure to follow the right procedure, so that you do not set your company up for an attack.
Verdict On The Best Honeypot Software
Now, you already know what honeypot is, how it works and the best honeypot software you can use. If you are a new player, it is not difficult to install and configure any of these honeypots. Just remember to do it in a testing network separate from your production system, at least for the first tests until you are confident enough.